Correct Answer

verified
Unauthorized use of a Wi-Fi network is c...View Answer
Show Answer
Correct Answer
verified
View Answer
True/False
Numeric passwords are also referred to passcodes .
B) False
Correct Answer

verified
Correct Answer
verified
True/False
A(n) denial of service (DoS) attack is an act of sabotage that attempts to flood a network server or Web server with so many requests for action that it cannot handle legitimate requests any longer.
B) False
Correct Answer

verified
Correct Answer
verified
Short Answer
A(n) ____________________ is a unique digital code that can be attached to a file or an e-mail message to verify the identity of the sender of a document.
Correct Answer

verified
Correct Answer
verified
True/False
Botnets are a major security threat since criminals are increasingly creating botnets to use for computer sabotage.
B) False
Correct Answer

verified
True
Correct Answer
verified
Multiple Choice
Like a computer virus, a ____ is a malicious program designed to cause damage.
A) computer worm
B) scam
C) phish
D) computer bug
F) None of the above
Correct Answer

verified
Correct Answer
verified
True/False
Private key encryption is also called symmetric key encryption.
B) False
Correct Answer

verified
Correct Answer
verified
True/False
Identification systems determine whether or not the person attempting access is actually who he or she claims to be.
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
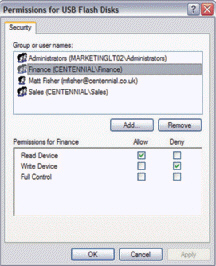 ____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine
F) A) and C)
Correct Answer

verified
Correct Answer
verified
True/False
Unauthorized use involves using a computer resource for unauthorized activities.
B) False
Correct Answer

verified
True
Correct Answer
verified
Essay
Discuss online auction fraud.
Correct Answer

verified
Online auction fraud (sometimes called I...View Answer
Show Answer
Correct Answer
verified
View Answer
Multiple Choice
A ____ is a malicious program that masquerades as something else-usually as some type of application program.
A) Trojan horse
B) computer worm
C) computer insect
D) computer bug
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A computer ____ is a software program that is installed without the permission or knowledge of the computer user, that is designed to alter the way a computer operates, and that can replicate itself to infect any new media it has access to.
A) phish
B) virus
C) bot
D) link
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
____ uses a single secret key to both encrypt and decrypt the file or message.
A) Private key encryption
B) Asymmetric key encryption
C) Public key encryption
D) Synchronous key encryption
F) B) and D)
Correct Answer

verified
Correct Answer
verified
True/False
AntiDoS software is used to detect and eliminate computer viruses and other types of malware.
B) False
Correct Answer

verified
Correct Answer
verified
True/False
Computer spyware includes any illegal act involving a computer.
B) False
Correct Answer

verified
Correct Answer
verified
Short Answer
In businesses, access control systems are often integrated into a comprehensive ____________________ system designed to manage users' access to enterprise systems.
Correct Answer

verified
IDM
Correct Answer
verified
Multiple Choice
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
A) spider
B) server
C) client
D) bot
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A ____ provides a secure private tunnel from the user's computer through the Internet to another destination and is most often used to provide remote employees with secure access to a company network.
A) laptop private network
B) USB private network
C) tunnel private network
D) virtual private network
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Short Answer
The purpose of a(n) ____________________ is to authenticate the identity of an individual or organization.
Correct Answer

verified
Correct Answer
verified
Showing 1 - 20 of 100
Related Exams