A) sudo
B) chmod
C) grep
D) pwd
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user's mobile device appears to be losing battery life rapidly and often feels warm to the touch, even when it is put away. The device is relatively new, so the user is concerned it is defective. A technician inspects the device and see the following: 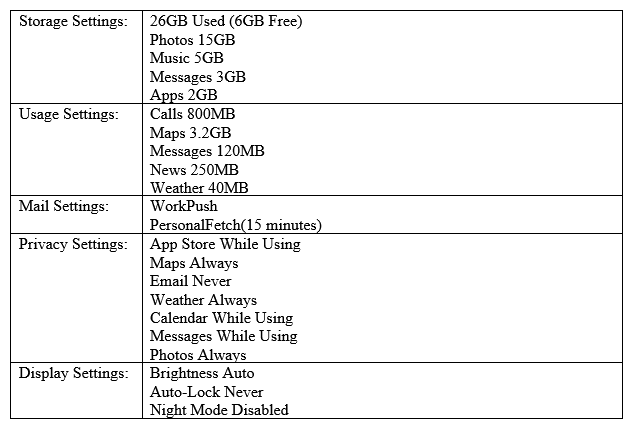 Which of the following should be changed to resolve this issue?
Which of the following should be changed to resolve this issue?
A) Privacy - Maps
B) Display - Brightness
C) Storage - Photos
D) Mail - Work
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A systems administrator creates a new folder in the user profile. The administrator wants it to have different NTFS permissions than its parent folder. Which of the following settings should the administrator change?
A) File attributes
B) Share permissions
C) Local share
D) Inheritance
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is the memory limitation of a 32-bit OS?
A) 16MB
B) 2048MB
C) 4GB
D) 1024GB
E) 2TB
F) 8TB
H) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user opens a phishing email and types logon credentials into a fake banking website. The computer's antivirus software then reports it has quarantined several temporary Internet files. A technician disconnects the computer from the network. Which of the following should the technician perform NEXT?
A) Have the user change the password.
B) Update the antivirus software and run scans.
C) Disable the user's local computer account.
D) Quarantine the phishing email.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security administrator does some network testing and identifies significant issues with security on desktop computers. As part of remediation, the network administrator is developing documentation based on best practices for applying updates to end users' computers. The network administrator must create the process documentation needed to submit back to the security administrator for approval. Which of the following process documents would the network administrator MOST likely create? (Choose two.)
A) Risk analysis
B) End-user acceptance
C) Backout plan
D) Plan for change
E) Business processes
F) Request for proposal
H) B) and F)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user is trying to install a very large .dmg file on a Windows computer but is receiving an error message. Which of the following is causing the error?
A) Small hard drive
B) Insufficient RAM
C) OS compatibility
D) Folder permissions
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user cannot print to a network printer. A technician runs the Windows 10 troubleshooting utility, but it does not find any errors. Which of the following printer settings should the technician check NEXT?
A) Duplex
B) Spooler
C) Collate
D) Resolution
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician is setting up a computer that needs to be configured so a few users can access it using Remote Desktop. For security reasons, the users should not be able to install software or change system settings. Which of the following Control Panel utilities should the technician use to accomplish this task?
A) Network and Sharing Center
B) Sync Center
C) Credential Manager
D) User Accounts
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A new business will be using credit cards in a physical location as well as its web presence. Which of the following does the business need?
A) PHI certification
B) PCI compliance
C) POTS implementation
D) PII filtering
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user's PC has been running slowly. The user says there have been no changes to the PC. Which of the following tools should the technician use to troubleshoot the cause of the speed reduction?
A) DxDiag
B) Windows Memory Diagnostic
C) Performance tab in Task Manager
D) Disk defragmenter
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician wants to write a script that will check data line by line until the end of the file. Which of the following elements will perform the check?
A) Loop
B) Integer
C) String
D) Variable
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user installed a new company-approved application on a Windows PC. The installation required a reboot. After the reboot and logon, the system froze. A technician has been called to fix the problem. Which of the following should the technician do FIRST?
A) Contact the application vendor support staff for more information
B) Boot into safe mode, and then load the ERD and restore the most recent files
C) Boot the PC, run msconfig , check the safe boot box under the Boot tab, and then restart Boot the PC, run msconfig , check the safe boot box under the Boot tab, and then restart
D) Log in as an administrative user and determine if the problem persists
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A computer running Windows 7 has an icon that has the appearance of an unlocked padlock with a yellow warning graphic. This icon advises the user that:
A) BitLocker is operating on the system but not for the user.
B) BitLocker has locked the drive, and it is no longer accessible.
C) BitLocker is suspended, and the drive is no longer encrypted.
D) BitLocker has encountered an error, and the user should run the check disk utility.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following should a technician do FIRST before opening a computer case to replace a part?
A) Remove all jewelry.
B) Put on an ESD strap.
C) Perform self-grounding.
D) Disconnect the power.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician arrives on site to find that two users who have the same model on Android smartphone are having the same issue with a specific application. Whenever they attempt to launch the application, it fails and gives an error message. Which of the following should the technician do FIRST?
A) Reinstall the application
B) Roll back the application to the earlier version
C) Clear the application cache
D) Update the OS of the smartphones
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An office location regularly experiences brownouts. Which of the following would be the MOST appropriate solution to protect the office computers?
A) Uninterruptible power supply
B) Voltage regulator
C) Surge suppressor
D) Generator
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A junior Linux system administrator needs to update system software. Which of the following shell commands would allow the administrator to gain the necessary permissions to update the software?
A) sudo
B) chmod
C) grep
D) pwd
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A Chief Executive Officer (CEO) is giving a presentation at an industry conference but forgot to bring a laptop. The company has emailed several large presentation files and the links to several videos that will be streamed during the presentation. While showing the last video, it starts to buffer, times out, and will not display. The CEO restarts the phone that is being used for the presentation and verifies there is enough free storage space, but the video still will not play. Which of the following is MOST likely causing the issue?
A) Data transmission over limit
B) Unauthorized account access
C) Resource over use
D) Unintended Bluetooth pairing
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
After a virus has been spread unknowingly via USB removable hard drives, a technician is tasked with limiting removable hard drive access to certain network users. USB ports are used for many devices, including scanners, printers, and signature pads, so a policy is created to deny access to removable hard drives only. When testing the policy, a removable drive is plugged in but can still be accessed. Which of the following command-line tools should the technician use to apply the new policy?
A) grupdate
B) diskpart
C) gpresult
D) net use
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Showing 301 - 320 of 409
Related Exams